Over the last few months we’ve been integrating H2O.ai’s flagship Agentic AI into GitHub and we’re excited to finally release the tool to the community.
We built the tool to enhance the developer lifecycle in GitHub. Simply tag @h2ogpte in a pull request or issue comment and let the world’s best agentic AI review your code, suggest changes and even open a new pull request. The tool is designed to integrate directly with air-gapped or managed cloud h2oGPTe instances, meaning your company’s code stays within your organisation, on your own hardware. However, even if you’re not a customer, you can try the tool using h2oGPTe freemium. To get started, follow our YouTube video and star our repository on GitHub.

Getting Started
To install the GitHub Action, run the following command in your terminal from the repository you’d like to install the action into:
curl -fsSL
https://raw.githubusercontent.com/h2oai/h2ogpte-action/refs/heads/main/installation.sh | sh -s < /dev/tty
Or, follow along in the installation video.
Use Cases & Examples
We use h2oGPTe GitHub Actions daily in our codebases and have recognised usage patterns across pull requests and issues. Here are a few ways you can use the action in your repository:
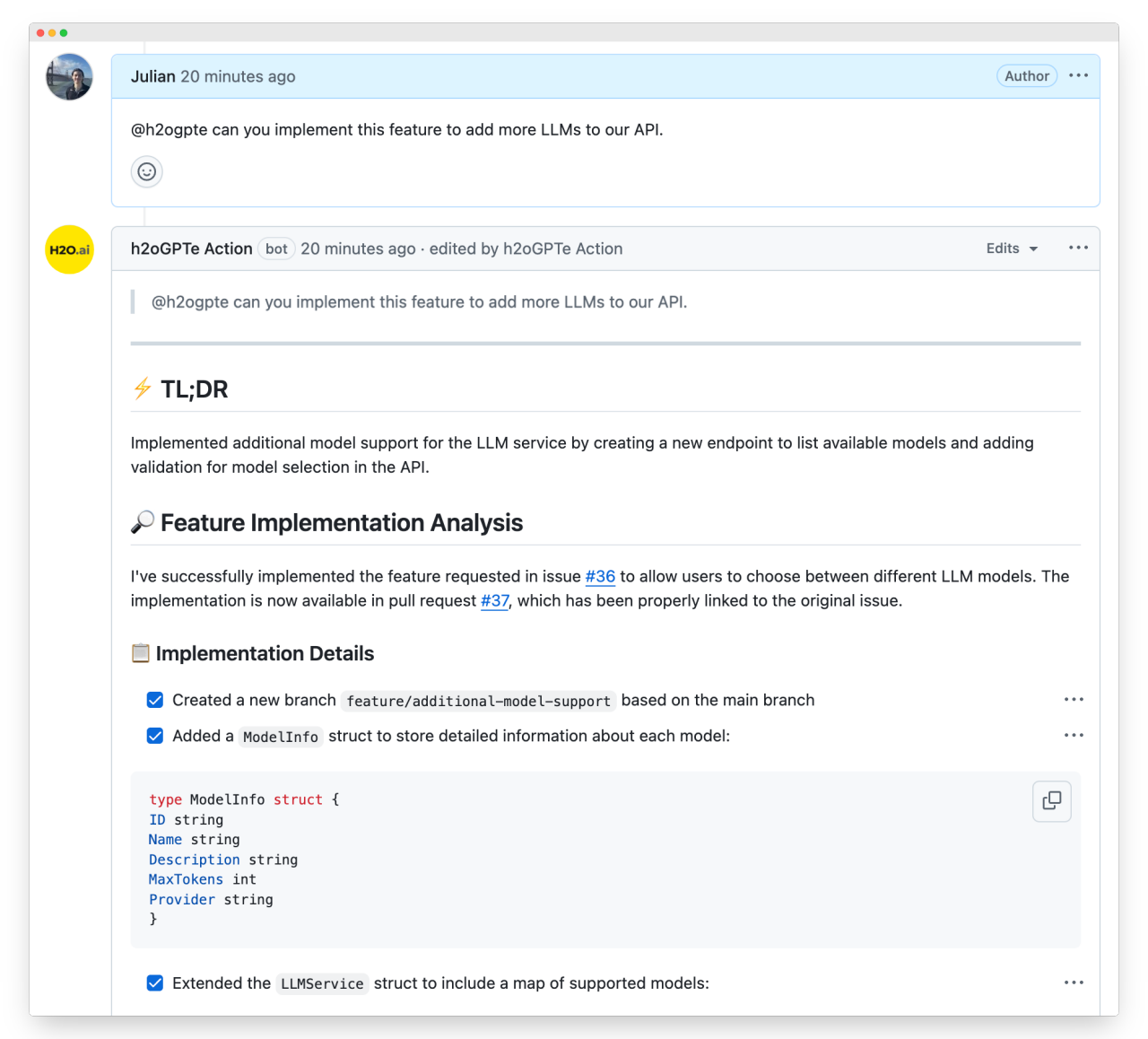
- Pull Request Comment
Leave a comment in a pull request mentioning @h2ogpte to trigger the action and receive AI-powered feedback.
Example:
None
@h2ogpte Can you review the changes in this PR and suggest improvements?
- Issue Comment
Mention @h2ogpte in an issue comment to get help or suggestions related to the issue.
Example:
None
@h2ogpte What are the possible causes for this bug?
- New Issue or PR Body
You can also mention @h2ogpte directly in the body of a new issue or pull request to automatically trigger the workflow.
Example:
None
This PR refactors the authentication logic. @h2ogpte please check for security issues.
- Adding Images
You can attach images to your comments or issues for h2oGPTe to analyse. For example, you might upload a screenshot of an error or a diagram:
Example:
None
@h2ogpte Can you help me understand this error?
[image attachment]
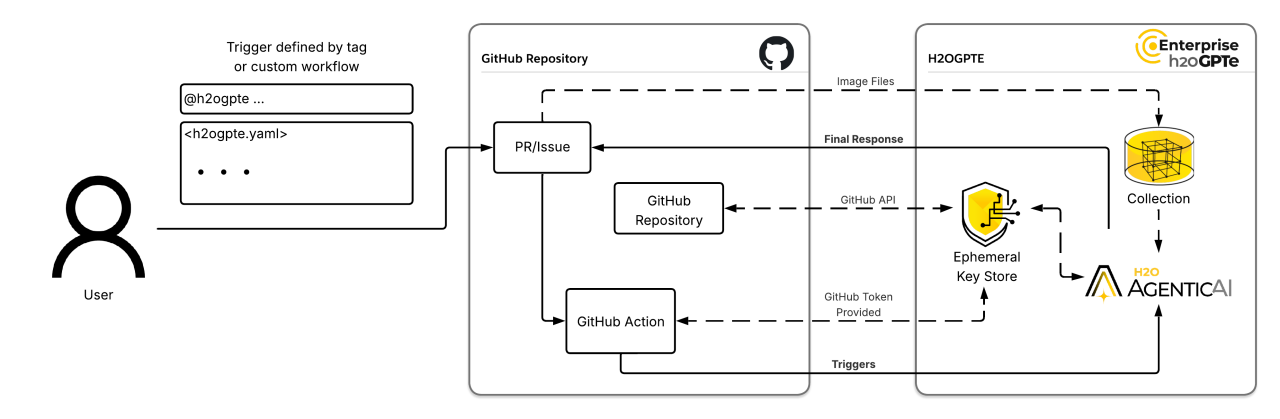
Architecture & Design
During development, we primarily focussed on fetching event data from GitHub’s REST and GraphQL servers and engineering the context of the Agent in h2oGPTe. We aimed to design the prompt to better reflect the layout of comments and pull request reviews in GitHub. In particular, we meticulously worked on sequentially organizing data retrieved from GitHub including the order of commit hashes and reviews in pull requests and images and linked events in issues.
Initially, we considered instructing the agent to fetch GitHub event data autonomously. This frequently resulted in high token usage and slower response times compared to pre-fetching the event data and conditioning the agent on the event context.
The action is also designed for enterprise usage. Hence, the action is configurable out of the box and interoperable with air-gapped environments. In our next release cycle, we’d like to focus on improving enterprise functionality by leveraging h2oGPTe’s in-built guardrails, MCP and evaluation features.
The full architecture diagram can be found below,